Ransomware
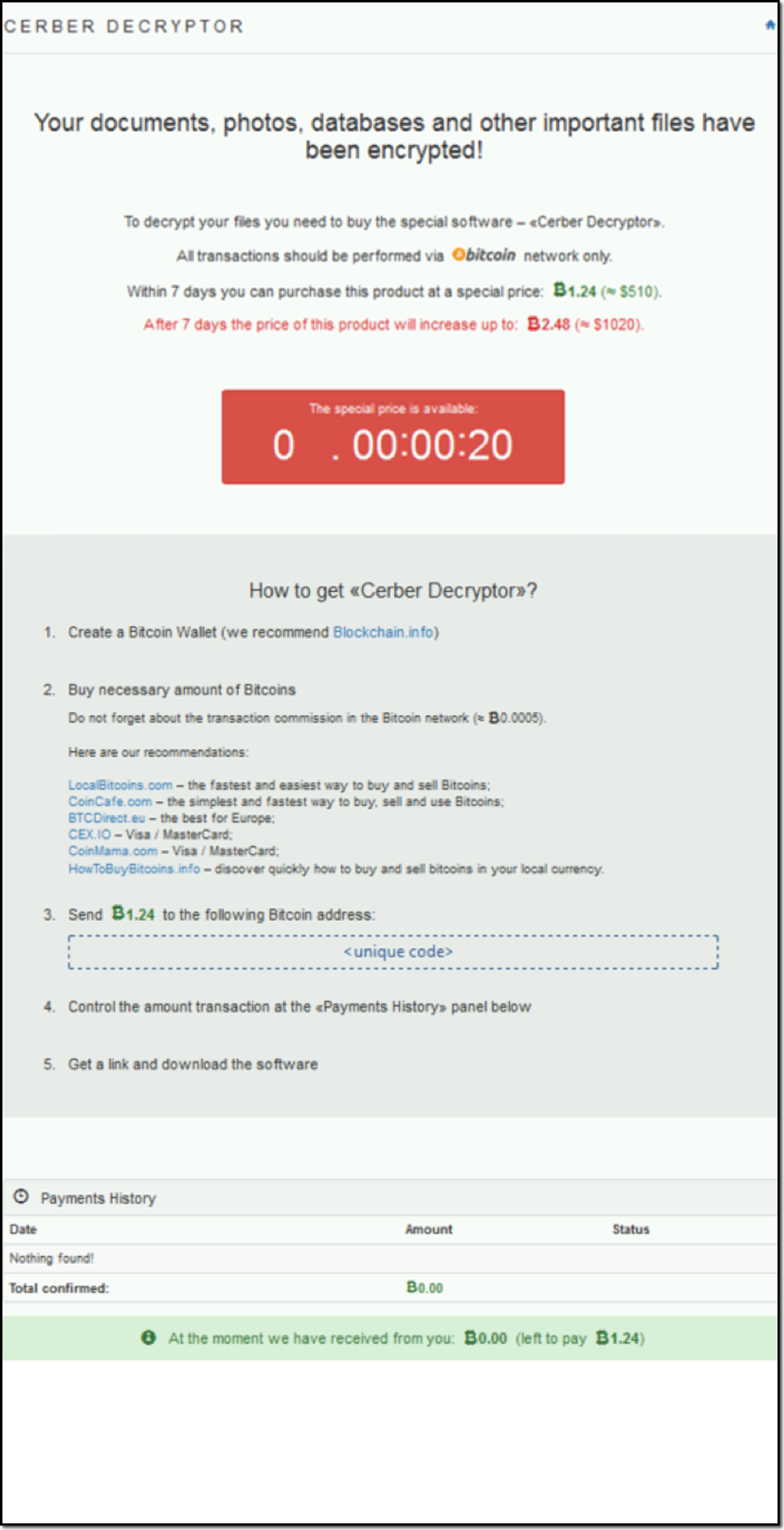
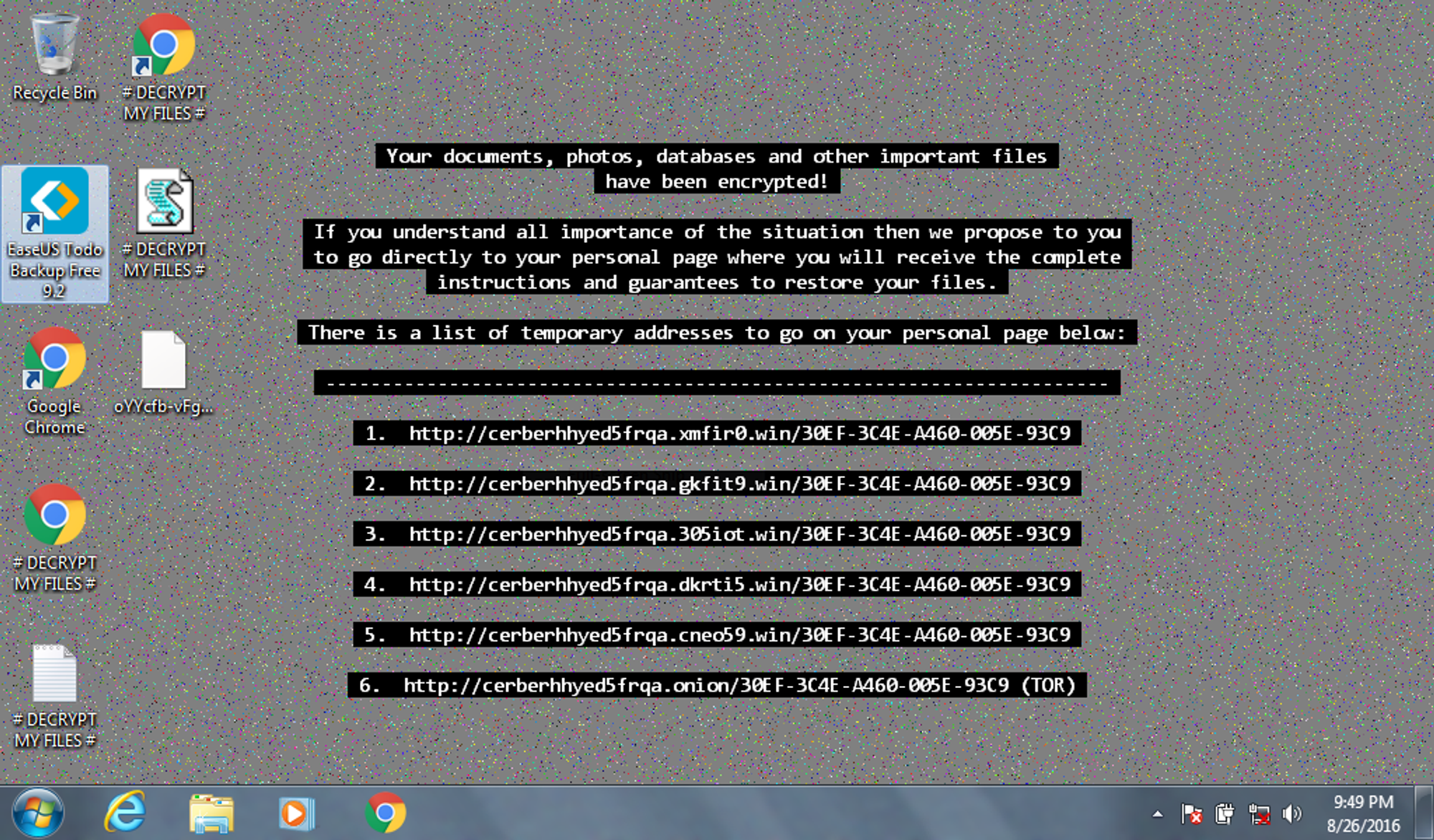
After the excitement of yesterday, Alice has started to settle into her new job. Sadly, she realizes her new colleagues may not be the crack cybersecurity team that she was led to believe before she joined. Looking through her incident ticketing queue she notices a “critical” ticket that was never addressed. Shaking her head, she begins to investigate. Apparently on August 24th Bob Smith (using a Windows 10 workstation named we8105desk) came back to his desk after working-out and found his speakers blaring (click below to listen), his desktop image changed (see below) and his files inaccessible.
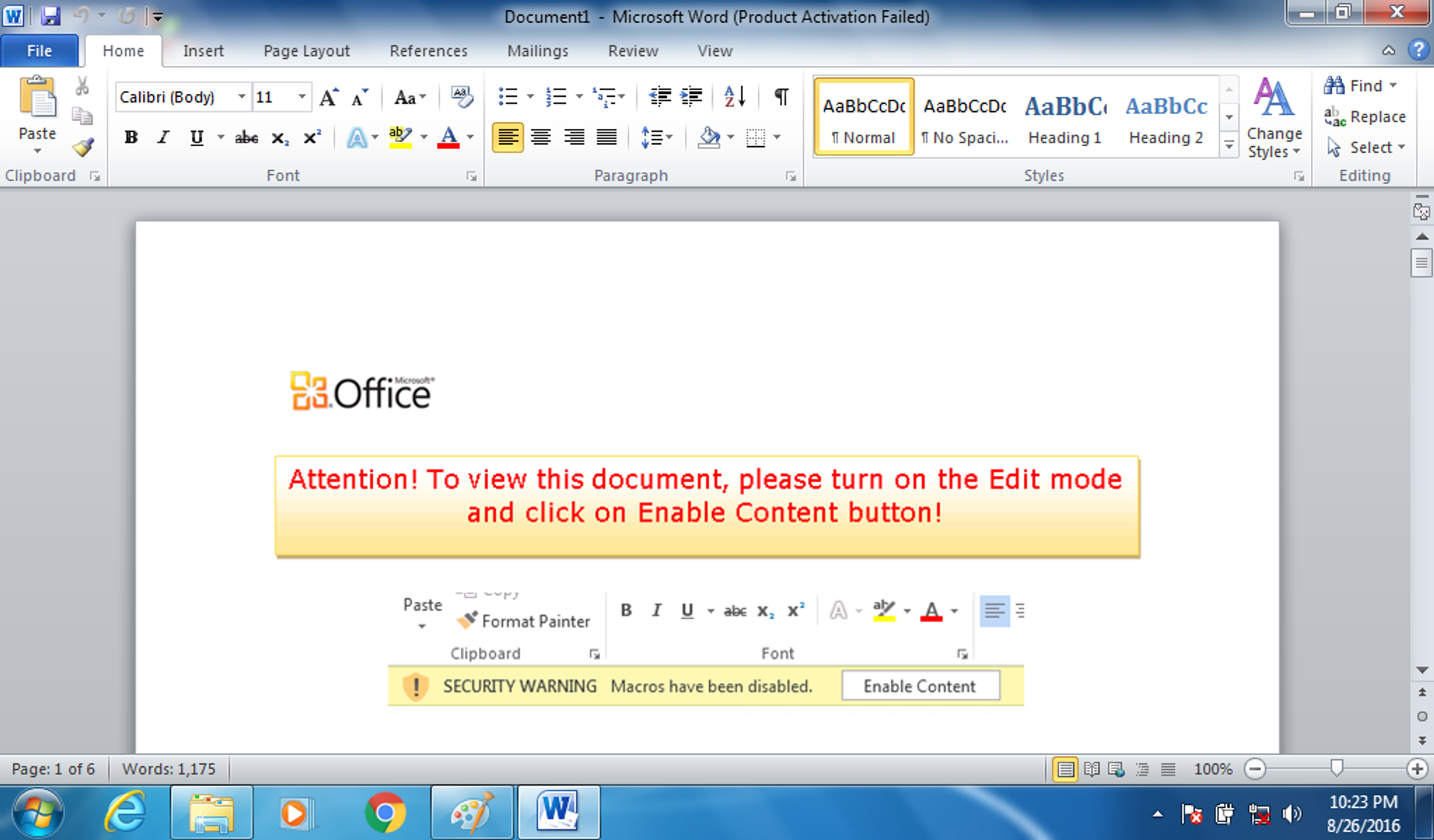
Alice has seen this before... ransomware. After a quick conversation with Bob, Alice determines that Bob found a USB drive in the parking lot earlier in the day, plugged it into his desktop, and opened up a word document on the USB drive called "Miranda_Tate_unveiled.dotm". With a resigned sigh she begins to dig into the problem...
어제의 흥분을 뒤로하고 Alice는 새로운 직장에 적응하기 시작했습니다. 슬프게도 그녀는 새로운 동료가 그녀가 합류하기 전에 믿게 된 크랙 사이버 보안 팀이 아닐 수도 있음을 깨닫습니다. 인시던트 티켓팅 대기열을 살펴보면서 그녀는 처리되지 않은 "중요" 티켓을 발견했습니다. 그녀는 고개를 저으며 조사를 시작합니다. 분명히 8월 24일에 Bob Smith(we8105desk라는 이름의 Windows 10 워크스테이션 사용)가 운동을 마치고 책상으로 돌아와 보니 스피커가 크게 울리고(듣기 위해 아래를 클릭) 데스크톱 이미지가 변경되었으며(아래 참조) 파일에 액세스할 수 없었습니다.
Alice는 이것을 전에 본 적이 있습니다... 랜섬웨어. Bob과 짧은 대화를 나눈 후 Alice는 Bob이 그날 일찍 주차장에서 USB 드라이브를 발견하여 데스크톱에 연결하고 USB 드라이브에서 "Miranda_Tate_unveiled.dotm"이라는 워드 문서를 열었음을 확인합니다. 체념한 한숨과 함께 그녀는 문제를 파헤치기 시작하는데...
Resources
Splunk server: https://gettingstarted.splunk.show
Credentials: user001-splk / Splunk.5
•
Ransomware screen shot: https://botscontent.netlify.app/v1/cerber-sshot.png
•
Ransomware warning: https://botscontent.netlify.app/v1/cerber-sample-voice.mp3
•
Bots v1 sourcetype summary: https://botscontent.netlify.app/v1/bots_sourcetypes.html
•
Splunk quick reference guide: https://www.splunk.com/pdfs/solution-guides/splunk-quick-reference-guide.pdf
•
Alices journal: https://botscontent.netlify.app/v1/alice-journal.html
•
Mission document: https://botscontent.netlify.app/v1/mission_document.html
OSINT Sites Used
Background
Here are the external sites that we use during the workshop. These are not the only sites that can help when performing an investigation during an incident but they are a good start if you are looking for some options. If you would like to learn more, check out Ryan Kovar’s blog called Workflowing Your OSINT. This post talks about using workflow actions in Splunk to more easily pivot to open source intel sources as desired as well as a really helpful listing of different sites to visit depending if you are looking for information on malware, domains, URLS, other other kinds of artifacts.
Resources
Web Sites
•
Google
•
Microsoft
•
VirusTotal
•
ThreatMiner
•
ThreatCrowd
•
DomainTools
•
Malwr
•
Robtex
What a Cerber Infected Endpoint Looks Like
Screenshots and Audio from Cerber-Infected Windows 7 Endpoint
Word Document upon initial open:
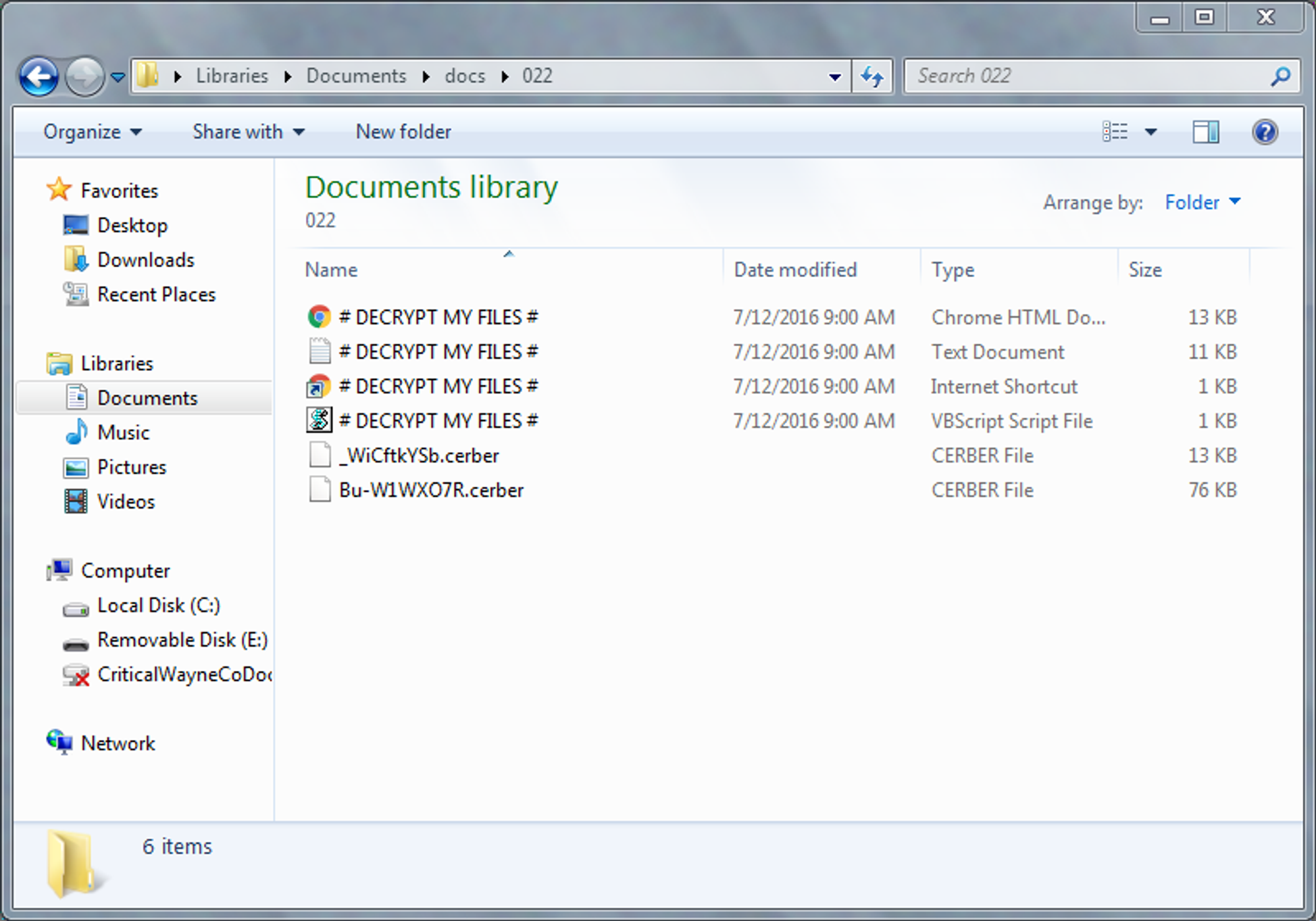
Windows Explorer directory after infection:
Windows Desktop after infection: